views
Removing on Windows
Open Start Windows Start. Click the Windows logo in the bottom-left corner of the screen.
Open Windows Defender. Type in windows defender, then click Windows Defender Security Center near the top of the Start window.
Click ☰. It's in the top-left corner of the window. A pop-out menu will appear on the left side of the window.
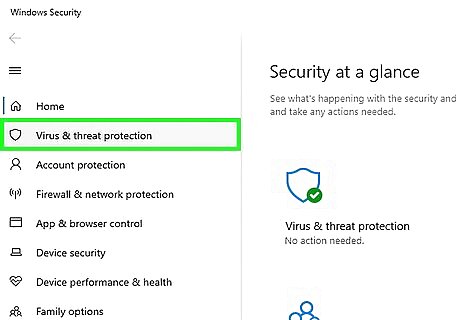
Click Virus & threat protection. This option is in the upper-left side of the pop-out window.
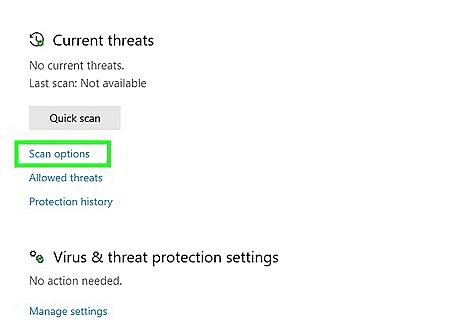
Click Advanced scan. It's a link in the middle of the page. Doing so opens the scan options page.
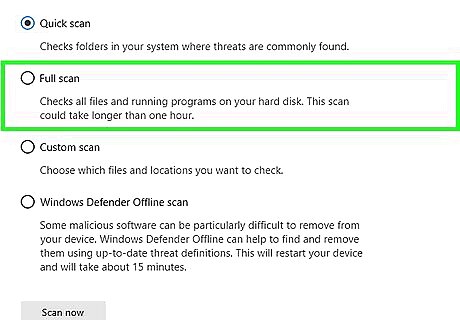
Check the "Full scan" box. You'll find this option near the top of the window.
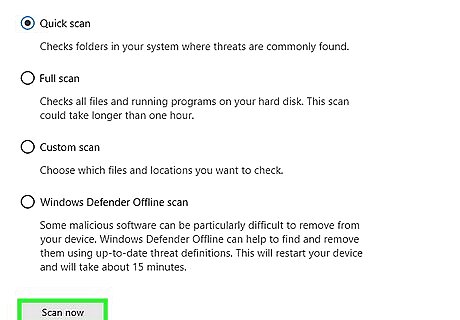
Click Scan now. It's near the bottom of the window. Windows Defender will begin scanning your computer for malware.
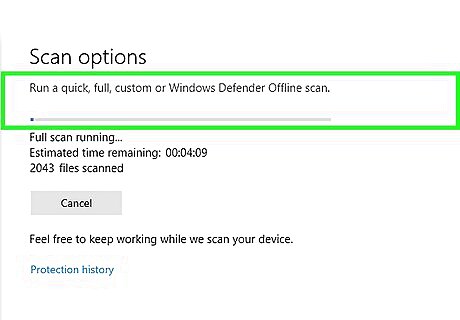
Wait for the scan to complete. If Windows Defender finds a trojan horse, it will quarantine and remove the trojan horse automatically, so you shouldn't have to confirm or perform any actions.
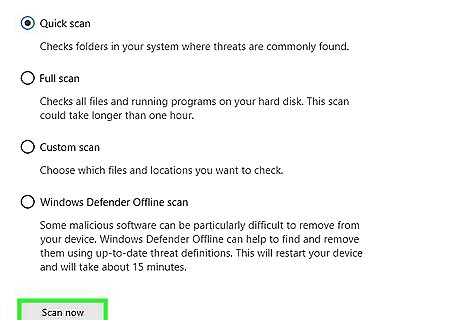
Perform an offline scan. An offline scan will remove particularly tricky programs and malware from your computer while your computer is offline. This scan will cause your computer to restart, and should take around 15 minutes: Click ☰ and click Virus & threat protection Check the "Windows Defender Offline Scan" box. Click Scan now Follow any on-screen instructions.
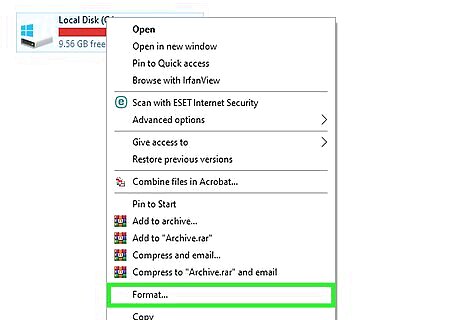
Remove and reinstall Windows. If running Windows Defender's scans don't remove the trojan horse from your computer, you will most likely have to format your hard drive by erasing and reinstalling Windows. Only do this as a last resort; you'll most likely lose some of your files. While you should back up as many files as possible before doing this, keep in mind that trojan horses often install programs or copy malware into your files. This means that you may have to manually back up your files rather than backing up your whole computer.
Removing on Mac
Download Malwarebytes for your Mac. Go to https://www.malwarebytes.com/mac-download/ and wait for Malwarebytes to begin downloading. Macs don't come with built-in antivirus software, but Malwarebytes is a solid option for all Mac users. If Malwarebytes doesn't begin downloading, click the blue click here link near the top of the page.
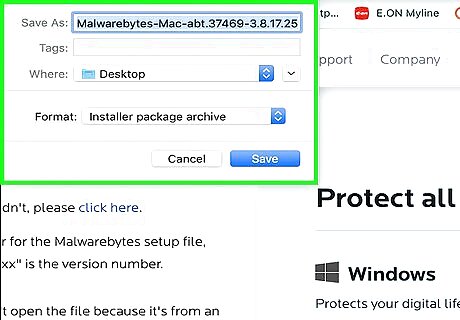
Install Malwarebytes. Double-click the Malwarebytes PKG file, verify the software installation if prompted, and then do the following: Click Continue Click Agree Click Install Enter your username and password. Click Install Software Click Close when prompted.

Open Malwarebytes. Click Spotlight Mac Spotlight, type malwarebytes into Spotlight, and double-click the Malwarebytes result at the top of the search results. Malwarebytes will open.
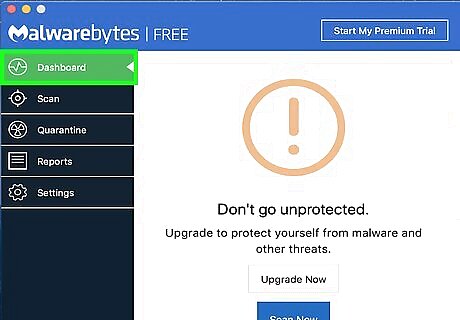
Click the Dashboard tab. It's in the upper-left corner of the Malwarebytes window.
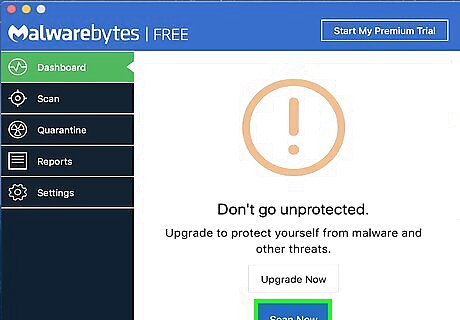
Click Scan Now. This button is at the bottom of the window. Doing so will prompt Malwarebytes to begin scanning your Mac for malicious software, including trojan horses. When Malwarebytes finds malicious software, it will automatically quarantine the software.
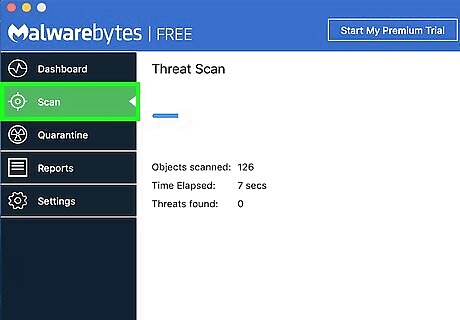
Click the Scan tab. You'll find it on the left side of the window once the scan completes.
Click Confirm when prompted. It's at the bottom of the Malwarebytes window. This will remove from your Mac any items that Malwarebytes has listed as malicious, including your Mac's trojan horse(s).

Remove and reinstall macOS. If running Malwarebytes doesn't remove the trojan horse from your computer, you will most likely have to format your hard drive by erasing and reinstalling macOS. Only do this as a last resort; you'll most likely lose some of your files. While you should back up as many files as possible before doing this, keep in mind that trojan horses often install programs or copy malware into your files. This means that you may have to manually back up your files rather than backing up your whole computer.
Avoiding Trojan Horses
Keep your computer updated. Trojan horses are big deals—especially on Mac computers—meaning that patches which immobilize or remove trojan horses are often released when a high-profile trojan horses infect multiple computers. Updating your computer will also keep your computer's security suite and firewall up to date, which will improve the chances of your security options preventing a trojan horse from downloading before it ever reaches your computer.
Avoid downloading files from third-party sites. Virtually all pieces of software originate on an authoring or "first-party" site (for example, the Steam program used by most PC gamers originated on and can be downloaded from the Steam website). Downloading software from any site other than the one on which it originated is risky, and can lead to accidentally installing malware. An exception to this rule is when a trustworthy first-party website lists a different site as its download location (or "mirror").
Don't use P2P or torrenting sites. For the same reason that downloading programs from third-party sites isn't recommended, using a torrenting (or P2P) site to download files can be incredibly dangerous for your computer. This is especially true when downloading cracked versions of programs since trojan horses almost always disguise themselves as installation files for other programs.
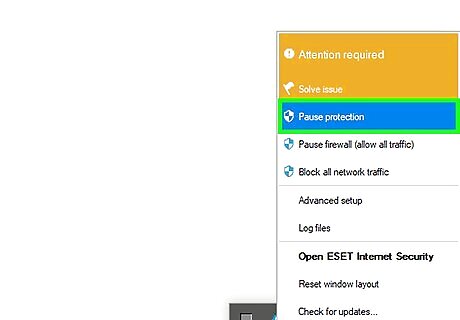
Refrain from disabling your antivirus or firewall. While some programs recommend making exceptions in your firewall or disabling your antivirus for a small period of time, doing so opens you computer to attacks and can be conducive to trojan horse installations.
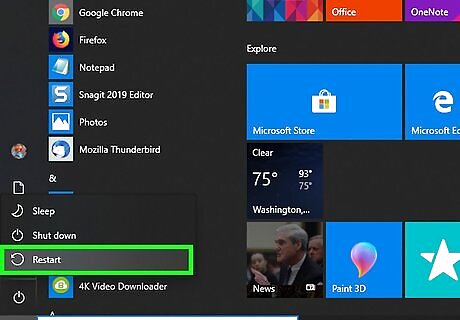
Remove troublesome programs in Safe Mode. Safe Mode restricts the number of programs which can run to only the most basic ones needed to run your computer; this will often disable programs which were installed by a trojan horse, allowing you to remove them without running into errors or having them come back later. You'll most likely want to use Safe Mode to remove things like unwanted toolbar programs (e.g., Bing).
















Comments
0 comment