
views
Identifying Sensitive Information

Protect any information your company has that others should not. As a business leader, it's important to be thorough in assessing what's sensitive and what is not. The specifics will vary from company to company, of course, but in general, you should take steps to secure anything that could damage your customers, your employees, or the success of your business if it was made public. For instance, you might need to protect personal information about your customers, such as their names, Social Security numbers, and credit card information. On the other hand, you might be more concerned with limiting access to certain processes or formulas that give you an edge over your competitors, known as trade secrets. This might include formulas or manufacturing processes, your company's financial model, lists of your suppliers, acquisition information, or your sales methods. When you're evaluating what information to classify as sensitive, also consider how long you'll need to retain that information. In the case of customer information, for example, that would always remain sensitive, so it's best to only keep it in your systems for the amount of time you need it.

Safeguard this data against threats like data theft or leakage. Don't just leave data security up to your IT department—it should be built into every aspect of your company. Make security a top priority, and keep in mind that data loss can occur from both outside and inside your company. This can lead to fraud, identify theft, the loss of revenue, the trust of your customers, and even legal trouble. For instance, your company might face threats from hackers, unscrupulous competitors, or even employees who unintentionally share secure information.

Beware of labeling everything as sensitive. While security should be a top priority, it's also important to create a company culture where your employees have the information they need to do their jobs. If you're generally transparent with your employees, they'll be more understanding about the information that you aren't able to share with them. If you label too much information as sensitive, employees will likely find workarounds for security protocol as a way to access the data they need.
Handling Protected Data

Know the legal requirements for handling sensitive information. There are a number of legal statutes that might affect how your company needs to treat sensitive data. These statutes can impact everyone from the company directors to front-line employees, so make sure everyone is in compliance. For example, if your company offers financial services like cashing checks or making loans, the Gramm-Leach-Bliley Act requires you to protect all nonpublic personal information, including consumers' names, addresses, payment history, or information you obtain from consumer reports. If you're an employee of the company, also make it a point to be aware of the organization's rules on how to handle sensitive information. Consider reaching out to an attorney who specializes in corporate law to be sure you're legally protected.

Communicate your business' expectations clearly to employees. Make security an integral part of your company culture. Give all employees a handbook or brochure covering your privacy expectations and their role in information security. In addition, have regular training for all of your employees on how to handle sensitive information. For instance, you might have annual security training, then send an email if any of your security processes are changed are updated. You might also put up signage at each of your company's locations to keep security at the forefront of your employees' minds. Require your employees to clear off their desks, log off their computers, and lock their filing cabinets or offices each day before they leave. Encourage your employees to report possible data breaches. You might even create an incentive program to reward employees who bring an issue to your attention!

Train your employees to spot and avoid phishing. Sometimes, hackers will send emails or make phone calls that are designed to seem like they're coming from inside the company when they're not. This is usually done in an attempt to gain access to secure data. Make sure all of your employees know not to ever give out sensitive information over the phone or through email. In addition, discuss how they can quickly spot phishing requests. For instance, if an email seems suspicious, the recipient should carefully check the domain that the email was sent from. Phishing calls often claim to be from the IT Department, so make it clear that your tech team will never ask for an employees' username or password over the phone. Employees who receive calls from customers should have a process for verifying a clients' info before discussing any account information over the phone.

Create internal systems for handling sensitive data. Start by doing a top-down assessment to identify the sensitive information that your company handles, as well as where you might be vulnerable to data loss. Then, create a written policy on how to secure that information, how long to keep it stored, and how to dispose of it when you don't need it anymore. Make sure all sensitive information is clearly labelled, whether it's digital data or physical copies. Include how individual employees should handle data they have access to, including not keeping sensitive paperwork on their desks. This is known as a clean desk policy.
Control who has access to sensitive information. Create a need-to-know policy where employees only have access to information they directly need to do their jobs. This includes limiting access to computer data as well as taking physical security measures like storing paperwork, ID badges, access keys, and security codes in locked rooms or filing cabinets. Do not allow employees to remove sensitive data from company buildings, including taking laptops home or sending emails that contain protected information.

Protect the information on employees' computers. Digital data loss is a huge threat to any company that handles sensitive information. Maintain up-to-date firewalls, encryption protocols, and anti-virus software. In addition, require all employees to use secure passwords that contain letters, numbers, and symbols. Other measures might include: Setting up company computers so they automatically time out after they've been inactive for a certain amount of time. Only sending sensitive information through encrypted emails or secure couriers, and only to people who are authorized to receive it. Always using secure printing. Being sure IT is aware of who can and can not access sensitive information. Applying the same security measures to employees who work from home.

Restrict how much data leaves the building by limiting laptops. In general, it's best to have employees use desktop computers, especially if there is secure information stored on them. If an employee does need to use a laptop to do their job, limit or encrypt any sensitive data that's kept on that machine. Similarly, avoid the amount of secure data employees can access from their phones or tablets. Install a remote wipe facility on laptops and other devices. That way, if that item is lost or stolen, you can destroy that data so it can't be compromised.
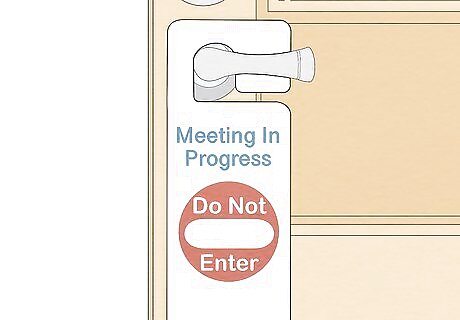
Ensure that sensitive discussions are kept secure. If there's a meeting in your company where trade secrets or other private information is going to be discussed, be sure it's held in a private room to avoid eavesdropping. In addition, be sure that only people who are authorized to know that information attend the meeting. For instance, you might use a private conference room with soundproof walls.
Don't keep sensitive data you don't need. There's no reason to risk losing sensitive data if it isn't anything essential to how your company runs. Don't accept or store unneeded private data from consumers, for instance—like using unique account numbers instead of identifying your customers by their Social Security numbers. If you have to gather sensitive information—like a credit card number—consider having it wiped from your system as soon as you're finished processing the transaction. Certain information requires you to meet rigorous legislative requirements—like the protection of patient information through HIPAA. Failing to meet those requirements can result in hefty fines, so if you don't need to handle or store it, it's best to avoid it altogether.

Have a plan for how to deal with a breach. The plan should detail how you'll keep your business running if there's some sort of security breach or data loss. This should also cover what the company will do to protect data in the event of a disaster that might leave your systems open to attack. For instance, if there's a widespread power outage, understand whether your digital data would be more vulnerable to hacking. If so, take steps to eliminate that risk.
Do regular audits to check security compliance. Have a plan to regularly assess who's been accessing what information—including within your IT department. Understand where your sensitive data is being stored on the system so you'll immediately know if anyone is trying to tap into it. Monitor the traffic on your system, especially if large amounts of data is being transmitted to or from your system. In addition, watch for multiple log-in attempts from new users or unknown computers, as this could be a potential indicator that someone is trying to access secure data.
Advising New & Departing Employees

Bind all employees with confidentiality agreements or clauses. Ask each new hire to sign a non-disclosure agreement (NDA) when they're brought on board—before they're given access to any trade secrets or client data. While this won't stop every instance of data loss, it does give you some legal protection in the event it occurs. Make sure the term for the NDA is sufficiently long enough to protect you even after the employee leaves the company.

Have a discussion about data security when someone is hired. Give new hires the handbook or brochure that spells out your security protocol. However, don't just expect them to read and understand it—explain it to them clearly during the onboarding process. Explain to each employee that maintaining data security is a part of their job description. Talk through any relevant laws and internal policy documents. Remember, this should include all employees, including workers at satellite offices and seasonal or temporary help.

Do an exit interview when an employee leaves. During this conversation, remind them of their NDA and what their obligations are surrounding any sensitive information they might have had access to. In addition, ask them to return their company devices, security badges, keys, and so on. Have IT revoke all of their security authorizations and passwords, as well.
Informing Third Parties and Visitors

Include sensitive information clauses in third party contracts. If you're doing business with any outside parties, like vendors and suppliers, be sure they're aware of their responsibility to protect sensitive information. In addition, make sure you're clear on when you're required to notify them of information that is considered private. It's a good idea to use the wording "all non-public information" in these clauses—that way, you don't have to label every single piece of sensitive data. You may also need to have your service providers sign NDAs if they'll be privy to sensitive information.
Share data only as-needed. Just like with your employees, make sure all third parties you're only giving information to third parties if it's absolutely essential to their ability to do their job. This is known as a "least-privilege" policy. In addition, make sure that information is only shared securely, like over encrypted networks or in private meetings. Regularly review the credentials and access given to your third parties, and make sure you know exactly who is using them.

Have visitors sign NDAS if needed. If a visitor to your company might potentially have access to secure information, have them sign a non-disclosure agreement when they check in. Store these visitor NDAs in a file for as long as they're valid in case an individual violates the agreements later. For instance, if a representative from your supplier will be touring your facility and they might get a glimpse of a non-public manufacturing process, it would be a good idea to have them sign an NDA.

Limit visitor access to secure information. While an NDA can give you some recourse if a visitor discusses private information, it's best to avoid allowing them access to that data at all. Have a policy preventing visitors from entering areas where secure information is stored, and monitor where they go while they're on the premises. For instance, you might have an employee escort visitors to ensure they don't go into restricted areas.
Storing & Disposing of Confidential Information
Be aware of how sensitive information comes into your business. In order to protect sensitive information, you need to understand the entry points. Assess where that information comes from, what it consists of, and who might have access to it. Some potential sources might include: For instance, you might get information from job applicants, customers, credit card companies, or banks. That information might enter your business through your website, email, the mail, cash registers, or your accounting department.

Securely store both digital information and paperwork. Data security requires a two-pronged approach. Not only do you need to protect your computer systems, but you also need to ensure that all paperwork is carefully secured. Ensure all paperwork is stored in locked filing cabinets, and that access is only given to authorized employees who legitimately need that information. In addition to securing your on-site digital data, ensure that all cloud storage uses multi-factor authentication and encryption.

Store digital information with care. When it's possible, avoid storing any sensitive data on computers that have internet access. In cases where you do need to have that information on a computer with an internet connection, be sure it's securely encrypted. You can also: Use secure servers, including cloud storage. Encrypt (or hash) client passwords. Regularly update passwords. Keep security software up-to-date. Be aware of software vulnerabilities. Control USB access. Back up information in a secure place.
Dispose of paperwork by shredding it. Don't just toss old applications or client files in the trash. Instead, invest in high-quality, cross-cut shredders and make sure they're easily accessible around the office. Then, have the shredded paperwork disposed of in confidential waste bins. Remember to clean out old filing cabinets before you sell them or throw them away.
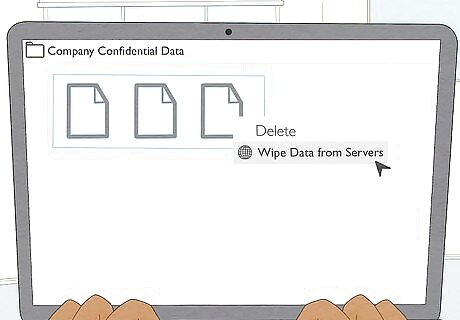
Completely erase hard drives before disposing of devices. Use a secure data destruction utility to ensure you destroy all of the information on the computer, phone, or tablet. Don't just rely on reformatting the hard drive—that isn't sufficient to completely wipe all of the data, even if you overwrite it afterward. You can also use a third-party data wiping program to be sure that files you routinely delete are erased from devices.


















Comments
0 comment