views
Google has removed nine apps from the Google Play app store after researchers at Dr Web anti-virus company found malware hidden in them. According to the security company, the nine apps had 5,856,010 downloads and possessed the ability to access users’ Facebook credentials through a sophisticated technique. These apps purportedly offered full-functionalities such as photo editing, app locker, horoscope updates, and more. Notably, all the identified apps offered users an option to disable in-app ads by logging into their Facebook accounts. After providing login details on the seemingly ‘genuine’ Facebook page, bad actors stole these credentials. The report does not highlight the number of users affected, but given the scale of collective downloads, the number could be in hundreds.
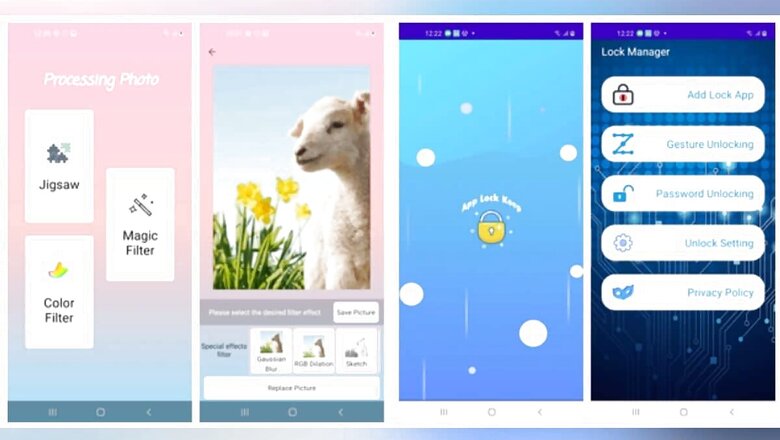
Dr Web shared the development in a blog post that notes that the most downloaded app was a photo-editing software called PIP Photo with over 5,000,000 downloads. Another photo-editing app, Processing Photo by developer ‘chikumburahamilton,’ clocked over 500,000 downloads and detected as Android.PWS.Facebook.13. The nine malicious apps include three ‘folder protection’ apps dubbed App Lock Keep from the developer Sheralaw Rence, App Lock Manager from the developer Implummet col, and Lockit Master from the developer Enali mchicolo ― all detected as Android.PWS.Facebook.13 malware. These three apps collectively had over 50,000 total downloads. Rubbish Cleaner from the developer SNT.rbcl ― a utility to optimise the Android phone performance had over 100,000 downloads. Astrology apps include Horoscope Daily by HscopeDaily momo and Horoscope Pi from the developer Talleyr Shauna with over 100,000 hits. Lastly, a fitness program called Inwell Fitness and detected as Android.PWS.Facebook.14 had more than 100,000 downloads. Dr Web notes that it discovered an earlier modification that was spread through Google Play under the guise of an image editing software called EditorPhotoPip, which has already been removed from the official Android app store, but could be still available via third-party websites.
The nine malicious apps purportedly carried the same trojan since they use identical configuration file formats and identical JavaScript scripts to steal user data. It is unclear how the nine apps ran past Google Play Protect that checks on apps before users download them. Once users provided Facebook login details to remove in-app ads, the trojans used a “special mechanism” to trick their victims. Here is how the company describes the process:
“After receiving the necessary settings from one of the C&C servers upon launch, they loaded the legitimate Facebook web page https://www.facebook.com/login.php into WebView. Next, they loaded JavaScript received from the C&C server into the same WebView. This script was directly used to highjack the entered login credentials. After that, this JavaScript, using the methods provided through the JavascriptInterface annotation, passed stolen login and password to the trojan applications, which then transferred the data to the attackers’ C&C server. After the victim logged into their account, the trojans also stole cookies from the current authorisation session. Those cookies were also sent to cybercriminals.”
Apart from Facebook login credentials, the attackers could have easily changed the trojans’ settings and commanded them to load the web page of another legitimate service, say Twitter or Gmail. This way, hackers could’ve accessed the credentials of multiple websites. Android users must delete these apps from the smartphone as soon as possible. The security company highlights that users must download apps from trusted developers.
Read all the Latest News, Breaking News and Coronavirus News here.















Comments
0 comment